
Bypassing SSL Pinning in Android Applications Using Frida
Learn how to bypass SSL pinning in Android applications using Frida
In today’s mobile security landscape, SSL pinning is a common technique used to protect the integrity of HTTPS connections in Android applications. However, for penetration testers and security researchers, it’s often necessary to bypass SSL pinning to analyze an app's network traffic. In this blog post, we'll explore how to bypass SSL pinning using the Frida framework, enabling you to perform Man-in-the-Middle (MitM) attacks on Android applications that enforce HTTPS connections.
What You Will Learn
In this tutorial, we will cover:
- How to configure and install a Burp Suite certificate on an Android device.
- How to connect your Android device using ADB (Android Debug Bridge).
- How to install and configure Frida Server.
- How to invoke a Frida script to bypass SSL pinning in your target application.
Step 1: Install the Burp Suite Certificate
The first step is to configure Burp Suite as your proxy and install its certificate on your Android device.
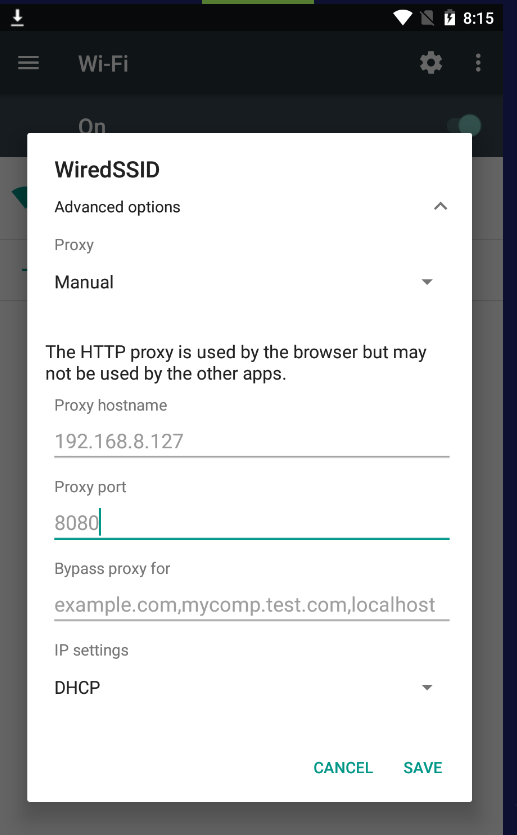
- Configure Burp Suite Proxy: Set up your proxy in Burp Suite. For this example, the proxy is configured with the bind address 192.168.8.127 and bind port 8080.
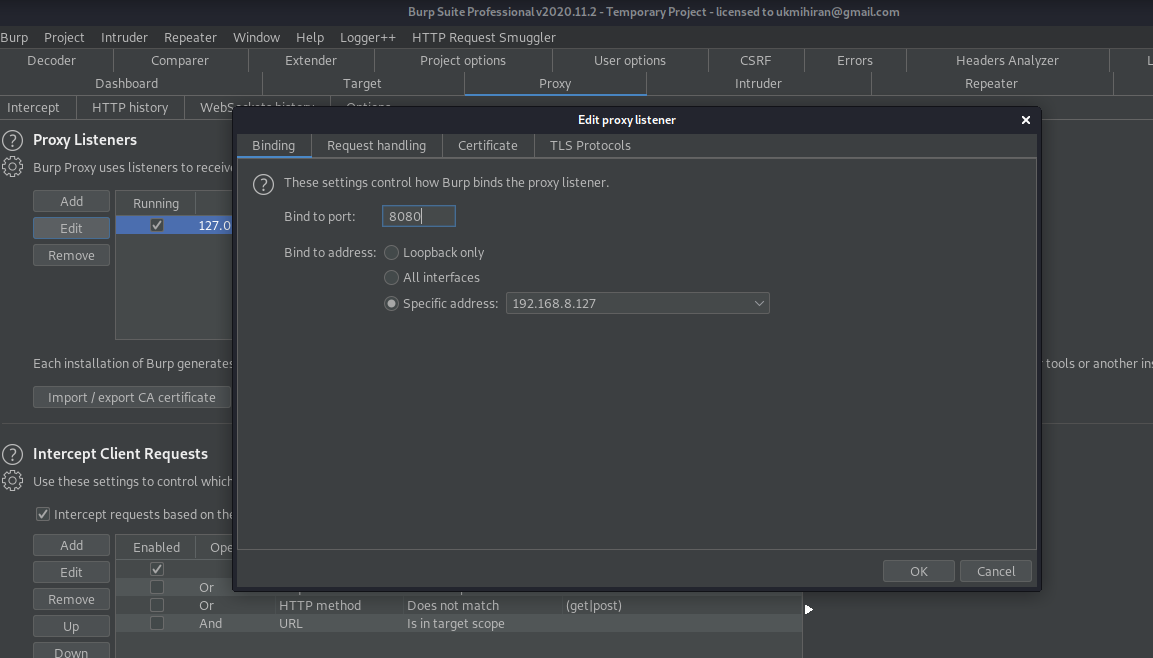
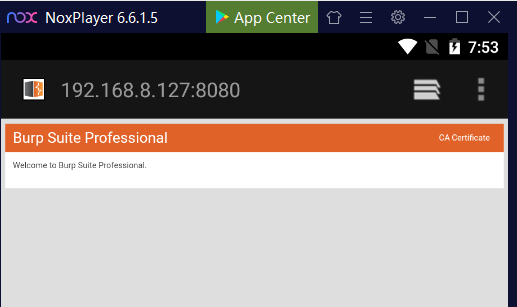
- Download the Burp Certificate: On your Android device, navigate to the proxy’s IP and port (e.g., http://192.168.8.127:8080) using a browser, and download the CA certificate by clicking on "CA certificate."
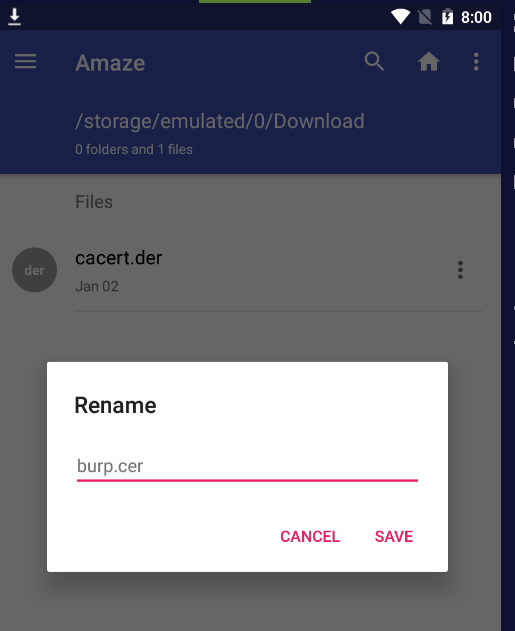
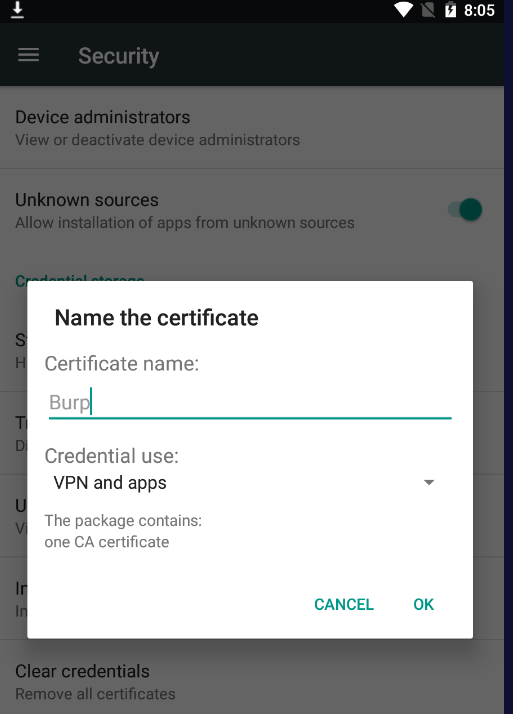
- Install the Certificate: Rename the downloaded certificate from cacert.der to burp.cer. Then, on the Android device, go to Settings > Security > Install from SD Card, locate the burp.cer file, and install it. You may be prompted to set a lock screen PIN or password.
- Configure Proxy Settings: On the Android device, go to Settings > Wi-Fi, long press on the connected network, and modify the network settings to use a manual proxy. Enter the proxy hostname (192.168.8.127) and port (8080).
Step 2: Connect Your Android Device Using ADB
To interact with the Android device from your computer, you’ll need to connect using ADB.
- Enable USB Debugging: On the Android device, enable USB Debugging from Settings > Developer Options.
- Connect via ADB: Run the following command to connect your computer to the Android device:
adb connect <IP address of the android device>- Verify the Connection: Ensure the device is connected by running:
adb devices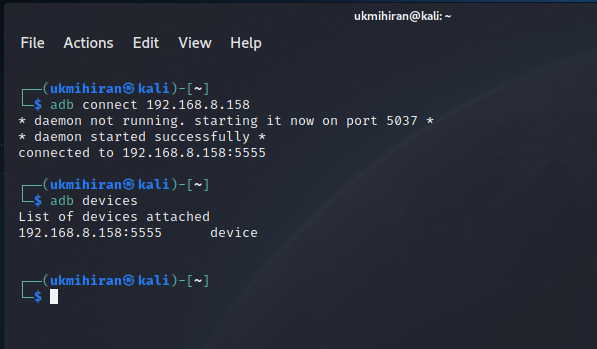
Step 3: Install and Configure Frida Server
Frida is a dynamic instrumentation toolkit that allows you to inject scripts into native apps. Here's how to set up Frida on your Android device:
- Install Frida Tools: Install Frida tools on your computer via pip:
pip install frida-tools- Verify the installation by running:
frida --help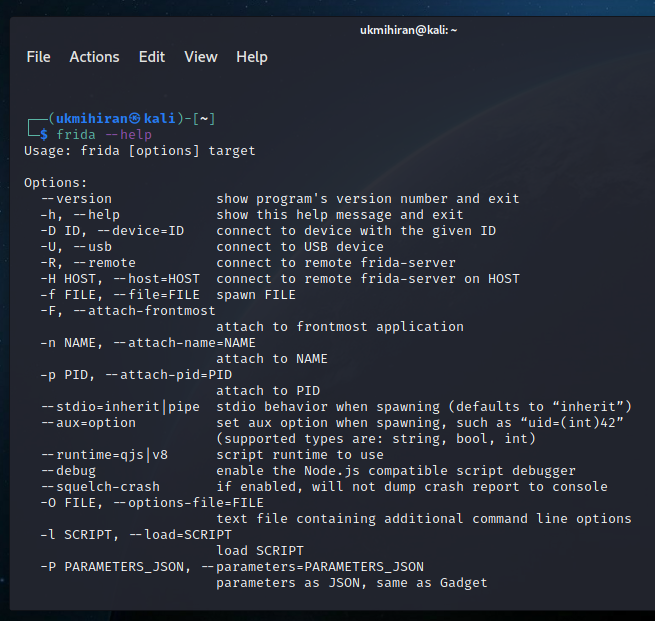
- Determine CPU Architecture: Find out the CPU architecture of your Android device with:
adb shell getprop ro.product.cpu.abi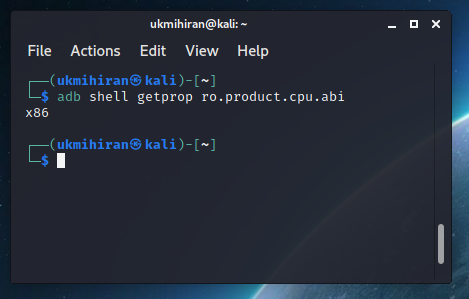
- Download Frida Server: Download the appropriate Frida server for your device's architecture from Frida releases. In this example, we download frida-server-14.1.0-android-x86.
- Transfer and Install Frida Server: Transfer the Frida server binary to the Android device using ADB:
adb push ./frida-server-14.1.0-android-x86 /data/local/tmp/frida-server- Set Permissions: Set the executable permissions on the Frida server binary:
adb shell "chmod 755 /data/local/tmp/frida-server"- Start Frida Server: Start the Frida server on the Android device:
adb shell "/data/local/tmp/frida-server &"- Verify the Server: Verify that the Frida server is running:
frida-ps -U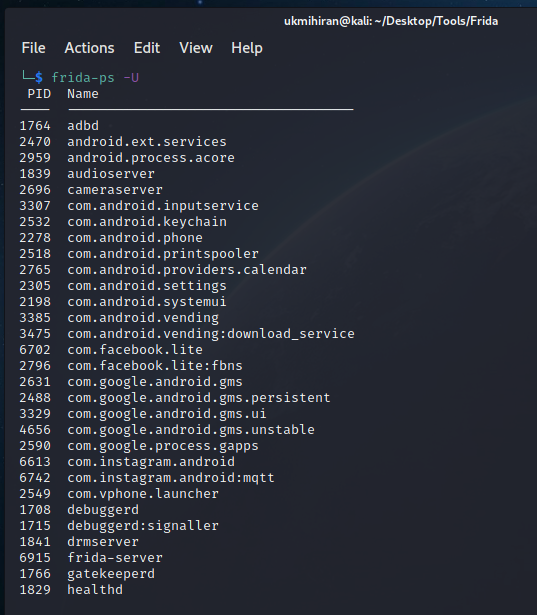
Step 4: Bypass SSL Pinning Using Frida
To bypass SSL pinning, you’ll need a Frida script that overrides SSL connections and uses your own Trust Manager.
- Get the Script: Download the SSL pinning bypass script from Frida Codeshare.
- Run the Script: Use Frida to inject the script into your target application. For this example, we'll target the Twitter Android app:
frida -U -f com.twitter.android -l sslbypass.js --no-pause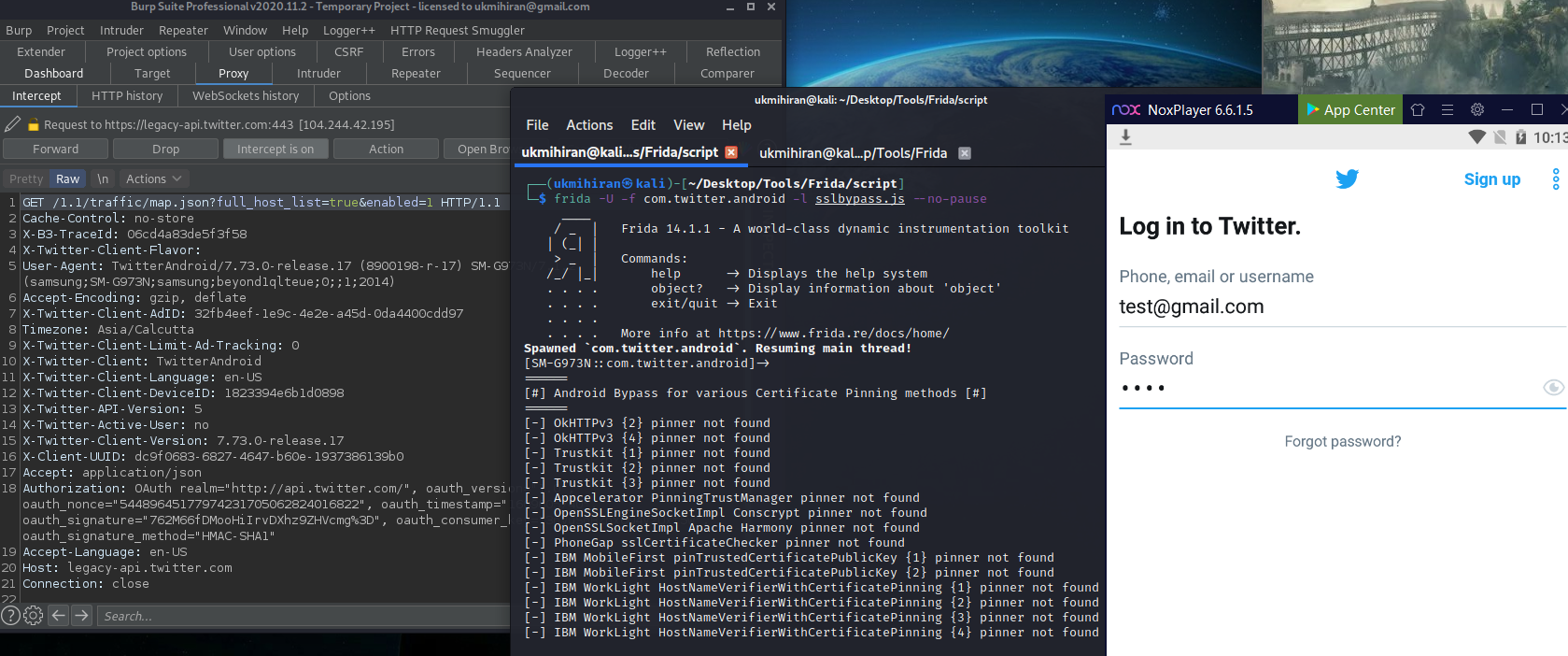
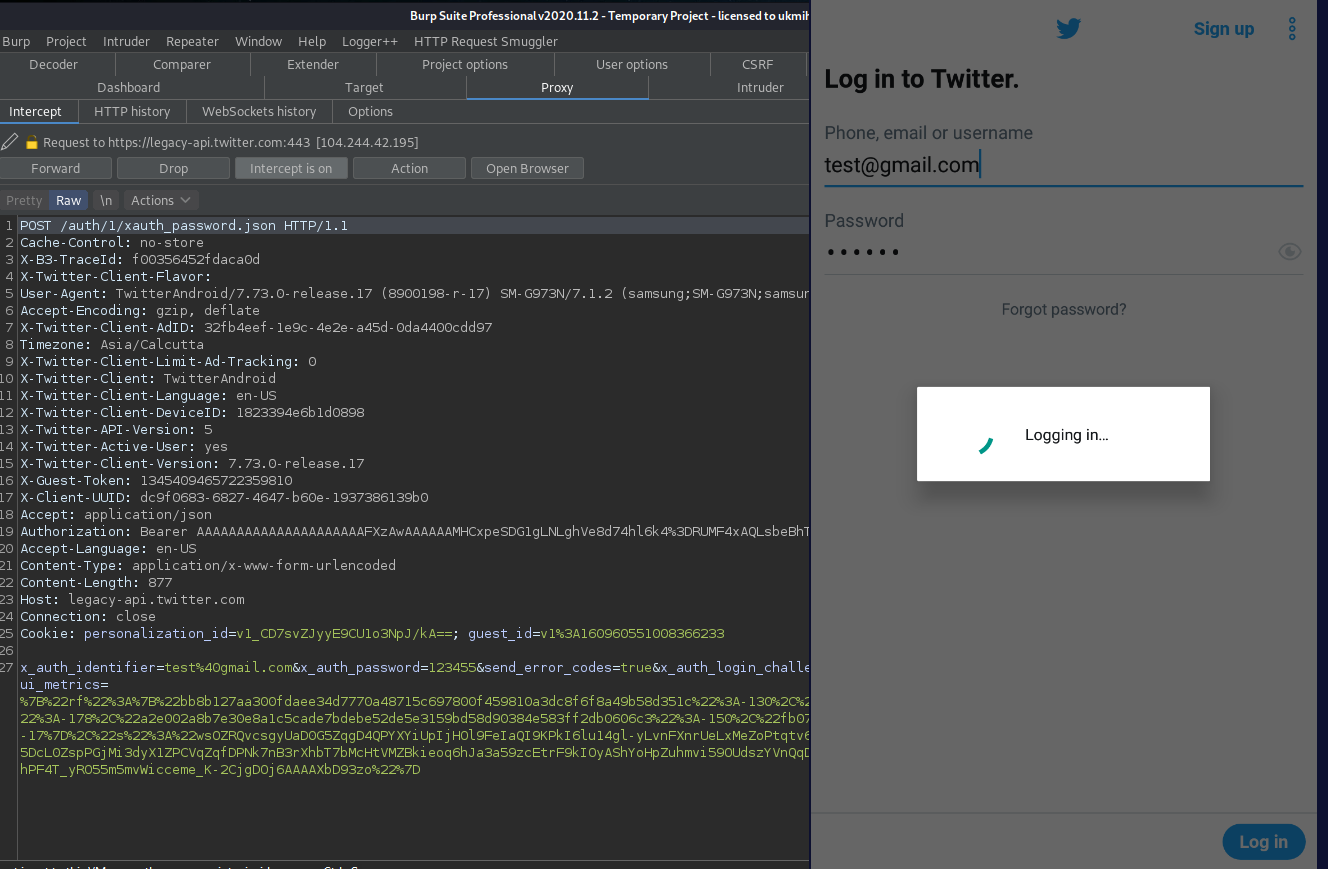
Once the script is successfully injected, all network traffic from the target app will be intercepted by Burp Suite, allowing you to analyze HTTPS connections. 😎
Conclusion
By following the steps outlined in this tutorial, you can effectively bypass SSL pinning in Android applications using the Frida framework. This method allows security professionals to perform MitM attacks on apps that enforce HTTPS connections, providing deeper insights during security assessments.
References
Related Articles

Apache Tomcat Server - Deserialization of Untrusted Data RCE
Introduction Apache Tomcat is a widely-used open-source implementation of Java technologies, including Java Servlet, JavaServer Pages (JSP), Java Expression Language, and WebSocket. In this post, we'll delve into a critical vulnerability found in Apache Tomcat
Udesh

Windows Service Privilege Escalation
Introduction In today’s tutorial, we’ll walk through a Windows privilege escalation technique that leverages insecure service permissions. This method is particularly useful when you’ve already exploited a vulnerability on a Windows machine using a publicly av
Udesh

Auth Bypass with PHP Type Juggling
Auth Bypass with PHP Type Juggling In this post, we will learn how to bypass authentication using PHP type juggling. Introduction PHP type juggling refers to the automatic conversion of data types during comparison operations. PHP offers two modes of compariso
Udesh